How To Use Remote IoT Behind Router: A Free Guide
Can you truly harness the power of the Internet of Things (IoT) from anywhere, anytime, without the constraints of location or complex setups? The answer is a resounding yes, as remote IoT access behind a router is not just a possibility, but a readily achievable reality.
In an era defined by unprecedented connectivity, the ability to remotely manage and control your IoT devices has become a cornerstone of modern convenience and efficiency. Whether it's overseeing smart home systems, monitoring industrial machinery, or accessing remote servers, the capacity to do so securely and effortlessly is invaluable. This guide delves into the intricacies of achieving this, focusing on how to use remote IoT behind a router, particularly in environments that may not have or prefer to avoid a reliance on Windows-based systems. We will explore various methods, tools, and techniques to empower you to take control of your IoT devices, offering a blend of practicality and expert insights for both novices and seasoned users. The goal is to provide a comprehensive understanding, equipping you with the knowledge and tools required to navigate the ever-evolving landscape of remote access.
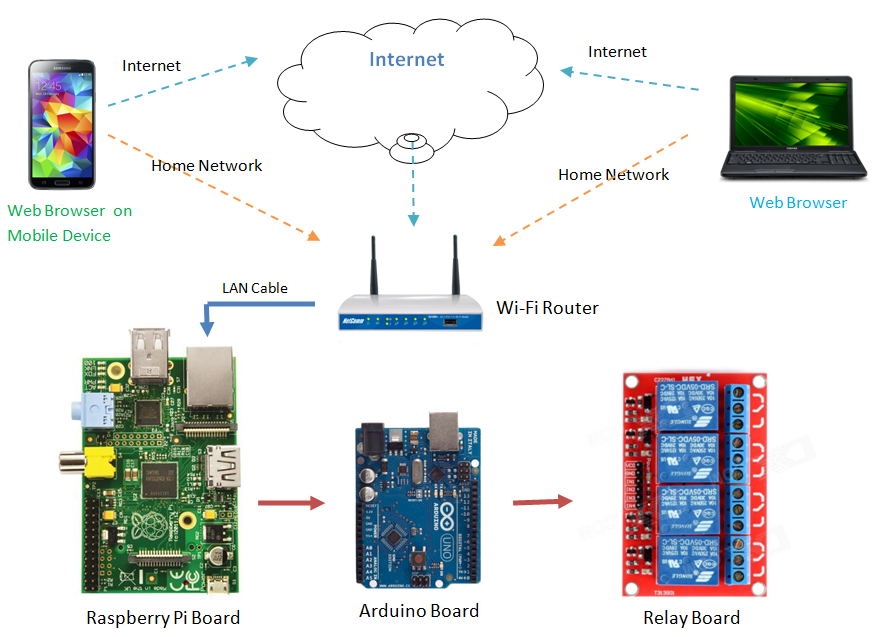
The landscape of remote IoT management is vast, and it can initially seem daunting. However, the core principles are surprisingly straightforward. The underlying concept revolves around establishing a secure and reliable communication channel between your remote device and your IoT devices that are behind the router. This typically involves configuring your router to facilitate external access and then setting up the IoT devices to respond to these external requests. The good news is, a Raspberry Pi can often be utilized, providing a cost-effective and flexible solution. Ultimately, its about ensuring that your devices can "talk" to each other, regardless of geographical location.
Before diving into specifics, it's important to understand the fundamental components involved. Consider the following scenario: You have a smart home system with several IoT devices perhaps smart lights, a thermostat, and security cameras all connected to your local network via a router. Your goal is to access and control these devices remotely from, say, a coffee shop or from your travels abroad. To achieve this, you need to address three key elements: the router, the IoT devices themselves, and an external point of access. The router acts as the gateway, translating external requests to internal devices. The IoT devices need to be configured to accept and respond to these requests, and the external point of access acts as the interface by which you will be able to command and interact with your system. There are multiple methods for this including, but not limited to, Dynamic DNS (DDNS), Virtual Private Networks (VPNs), and Secure Shell (SSH) connections. By understanding these components, you can then evaluate which tools and methods best fit your needs, experience level, and specific situation.
One of the simplest and most cost-effective approaches to achieving remote IoT access is through Dynamic DNS (DDNS). This method is particularly useful when your internet service provider (ISP) assigns a dynamic IP address, which changes periodically. Because these IP addresses change, it can be difficult to keep track of the address when youre trying to access your devices remotely. This is where a DDNS service comes in. A DDNS service provides a static hostname that always points to your current IP address, even when the IP address changes. To set up DDNS, you need to: 1) Choose a DDNS provider (there are many free and paid options available); 2) Create an account and configure your hostname with the provider; 3) Configure your router or IoT device to update the DDNS service whenever your IP address changes. Once configured, you can use the hostname to access your IoT devices remotely. This method is relatively simple to set up and doesnt require significant technical expertise.
Another powerful method for accessing remote IoT devices involves setting up a Virtual Private Network (VPN). A VPN creates a secure, encrypted connection between your device and your home network. When you connect to your home network via a VPN, your device acts as if it's physically present on that network. This allows you to access your IoT devices as if you were sitting in your living room. To set up a VPN, you will typically need a VPN server (often a router with VPN capabilities, or a dedicated device like a Raspberry Pi), and a VPN client on the device you will be using to connect remotely. The router should be set up and configured to create a VPN server that allows external devices to connect. The main benefits are that a VPN creates a secure and private tunnel that encrypts all data transmission. However, it may require more technical configuration depending on the VPN software. The key steps involve setting up a VPN server on your router (or a dedicated device), configuring the router to allow incoming VPN connections, and installing the VPN client software on the device from which you will connect remotely.
Secure Shell (SSH) is another robust way to securely access your IoT devices. SSH provides a secure method of remote login and allows you to execute commands on the remote device. To utilize SSH, the IoT device must support SSH, and SSH must be enabled and configured on the device. Using this method, you connect to your devices via SSH from anywhere in the world. By leveraging SSH, you get a direct line of command to your devices operating system, and that allows you to monitor, control, and manage your device. This is especially useful if you need to make changes to system settings, update software, or troubleshoot issues. However, it requires you to have some familiarity with the command line interface. Also, its very important to secure your SSH connection with a strong password or, ideally, SSH keys to prevent unauthorized access.
For those preferring a more visual interface, setting up a Virtual Network Computing (VNC) server on a Raspberry Pi is a great approach. VNC allows you to view and interact with the graphical user interface (GUI) of your Raspberry Pi from any device with a VNC client application. This is particularly useful if your IoT devices are connected to a Raspberry Pi, and you want to manage them from a distance. To configure VNC, you will need to install a VNC server on your Raspberry Pi. After that, you download a VNC client application on your device of choice (phone, tablet, or laptop). You would then connect to the Raspberry Pi using its IP address or hostname and your security credentials. This will enable you to see and interact with the Raspberry Pi's desktop, allowing you to manage your IoT devices through the same interface as you would if you were sitting in front of the Pi.
The ability to use Remote IoT behind a router with Mac filtering is another method of securing the access to your devices. MAC filtering adds an additional layer of security by restricting network access to devices with specific MAC addresses. To implement this, you will need to follow a few key steps. First, you'll need to identify the MAC address of the IoT device you want to access. This can usually be found in the device's settings or documentation. Next, you will need to access your routers configuration interface (typically through a web browser). Within the routers settings, you will then enable MAC address filtering and add the MAC addresses of the IoT devices that you want to allow access. This will block all other devices from connecting to your network, improving its security. This method works as an added layer, however, it does not replace other security protocols like strong passwords or encryption.
When working remotely it is important to remember that the security of your IoT devices is of paramount importance. Because you are opening up your network to external access, you must ensure your systems are secure from unauthorized access. Begin by using strong, unique passwords for all your devices, including your router and IoT devices. The use of multi-factor authentication can add additional security for your accounts. Keep your software updated. Regularly update the firmware of your router and the software on your IoT devices. Software updates often include security patches that address vulnerabilities. Always be wary of unsolicited emails and avoid clicking links or downloading attachments from unknown sources. Moreover, consider isolating your IoT devices on a separate network segment (VLAN) to prevent potential security breaches from affecting your main network. Use encryption where possible, such as using a VPN, SSH, or HTTPS to encrypt communications.
Troubleshooting common issues is an important part of the process. For example, if you can't connect remotely, start by checking the basics. Are the devices powered on and connected to the network? Double-check your internet connection. Make sure your router is configured correctly for port forwarding (if required). Ensure your firewall isnt blocking the connection. Verify your DDNS configuration, and test your hostname. For VPNs, ensure that the VPN server is running, and the client is properly configured. Verify that there are no conflicts in IP addresses, and that all relevant ports are open on your firewall. For SSH connections, verify that SSH is enabled on the remote device, and that your SSH client is properly configured with the correct IP address or hostname, port number, and user credentials. Remember to review the error messages, as they can often give you valuable clues. If youre still experiencing issues, consult online forums and communities for support, but make sure you trust the source.
The landscape of IoT is ever-evolving, and so too are the tools and software available. The remoteiot platform is one such tool. The remote IoT platform allows users to remotely control IoT devices using a web browser. This can be a very convenient option for those who prefer a user-friendly interface. The beauty of the web browser is that it can be accessed from virtually any device with an internet connection. There are other remote management IoT platforms available as well. Some platforms also offer features such as data logging, device monitoring, and remote firmware updates. When choosing a platform, consider your specific needs and technical skill level. Some platforms are designed for ease of use, while others offer more advanced features for experienced users. Explore the available options, considering their features, pricing, and support documentation. Researching reviews and feedback from other users can provide valuable insights into the platform's reliability and ease of use.
The deployment of IoT devices is increasing, along with the number of users looking to manage those devices from a distance. To stay ahead in this evolving environment, users must be equipped with a variety of tools and understanding. By understanding the basics of IoT networking, you can begin your journey to remote access. While the learning curve may take time and patience, the ability to troubleshoot common issues is also very important. The first step that well want to accomplish is setting up remote access to the cellular router itself. Additionally, remote SSH access can also be helpful if the device supports it. This guide is a starting point; stay informed, and explore new technologies and methods as they emerge. Remote IoT access is no longer a futuristic concept, but a practical and achievable goal. By embracing these tools and techniques, you can unlock the full potential of your IoT devices from anywhere in the world, completely free of charge.